Protect your (login) data with MFA
Why multi-factor authentication?
How does multi-factor authentication work?
By implementing several security steps, your employees have to prove (‘multi-factor’) that they are effectively the ones who are trying to log in.
This is done on the basis of a two-stepped approach:
1
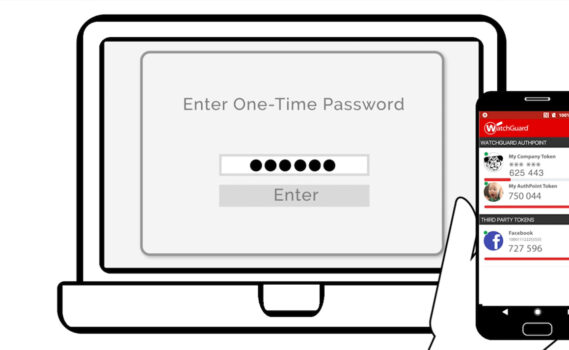
Enter your password and log in, as you already do today.
2
Approve a notification on your mobile phone, enter a code from a hardware token (such as the codes on your bank's card reader) or enter a one-time extra password.
With one simple extra step, it has become nearly impossible for a hacker to log in: after all, he has no access to the mobile phone, hardware token or the extra password. Easy, safe and fast! So with a small change you have brought a huge improvement to your security.
Curious to find out more or do you want to implement this in your own company? Then make sure to contact us. As a WatchGuard certified partner we can easily help you. This way you can take a huge leap forward in securing your environment and data in no time.
Free Dark Web Scan
Hackers enter your network, among other things, by stealing login credentials. That is often much easier for them than we think. Often the ‘weak links’ in IT security are human errors. These ‘security holes’ are therefore separate from any solid protection that is needed against more technically-oriented attacks. There are plenty of examples of highly counterfeit, rogue emails and login pages circulating that are difficult to distinguish from the legitimate version. In addition, when the personal data is stolen, it is also often exposed on the Dark Web.
In collaboration with WatchGuard we offer you the possibility to receive a Dark Web Scan report for free. Click below to check via the WatchGuard Dark Web Scan whether your company login details are still private. In this free and personalized Dark Web report you can see which email accounts were compromised. Of course we are happy to make an appointment with you to go through the report. If no hacked accounts were found for your domain, you will not receive a report. That is of course good news. But as always, preventing is always better than curing. With a security audit you will quickly find out where any other weaknesses in your IT security are located. Request your audit here.
What is the Dark Web?
Key Benefits of Multi-Factor Authentication
MFA goes beyond 2FA
Lots of integrations
Ease of use
Fast VPN and Remote Access Implementation
Frequently asked questions about multi-factor authentication
What if the smartphone with the AuthPoint app is lost or stolen?
Can I still log in without my smartphone?
Can I still log in if I don’t have any internet access?
I do not want to use my (private) smartphone for MFA. Are there alternatives?
For which (3rd party) services can AuthPoint be used?
Case: when a strong password is not enough
We share a recent real-life example to illustrate what you should pay attention to.
Our team of account managers is ready to help you

Christian

Jordan

Jurgen

Didier

Jean-Marc

Kaj