Case: when a strong password is not enough

Case: when a strong password is not enough
There are plenty of examples circulating of highly counterfeit, rogue emails and login pages that are difficult to distinguish from the legitimate version. We regularly encounter cases where employees have their login details stolen. On top of that, when this happens, that data is often exposed on the Dark Web.
In collaboration with WatchGuard we offer you the possibility to receive a Dark Web Scan report for free. Click below to check via the WatchGuard Dark Web Scan whether your company login details are still private.
Be careful with login credentials!
We share a recent real-life example to illustrate what you should pay attention to. This user had a long and complicated password set on his Microsoft 365 account.
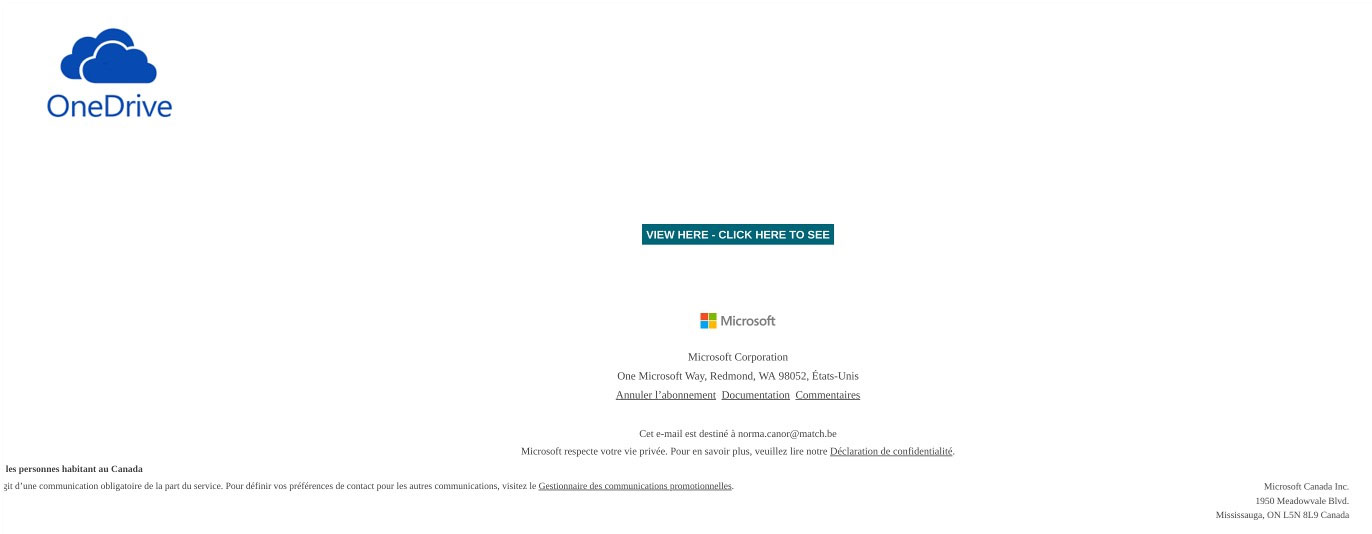
This person received the above email which seems to be sent from Microsoft OneDrive. At that time, coincidentally, the client was expecting a quote . By clicking on this, a well-crafted web page was requesting the Microsoft 365 login information.
Tip
By hovering over the link with the mouse, you can see the link to which you will be forwarded.
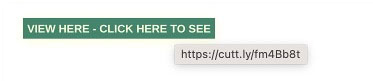
You can see that the link above is not a Microsoft link. In addition, there are also quite a few examples of so-called ‘Character lookalikes’, where the letters look very similar. For example k-force.be and κ-force.be. Unfortunately, the person in our example clicked through and entered the login details. Then all kinds of malicious files were placed in OneDrive.
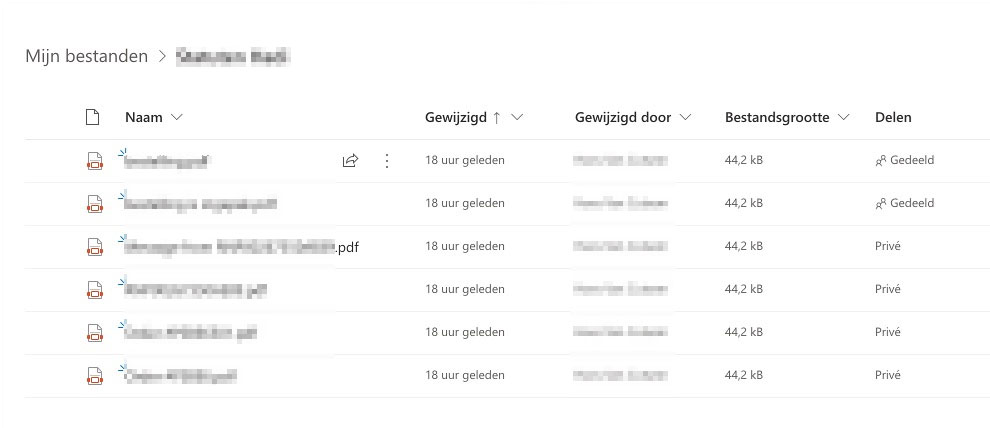
Immediately afterwards, the contacts in the client’s address book also received the same type of e-mail. At that time, the hackers had access to, among other things, the mailbox, so that e-mailing was possible. Perhaps among the recipients of all those e-mails there were also several people who, in turn, also entered their login details, and so the phishing attempts continue to spread.
The hackers also gain access to important and potentially sensitive company information, because they have access to the entire Microsoft 365 environment of at least one user.
The solution thanks to one extra step
With ‘multi-factor authentication’ we add an extra step to the login process. The rightful owner of the account will then receive a request for approval with every attempt to log in with his login details, for example on a smartphone. Under optimal circumstances, this step cannot be circumvented by hackers, because they do not have access to the connected smartphone.
Want to know more about multi-factor authentication?
From this example you can conclude that passwords alone are no longer secure enough. MFA is the solution, and we can help you in setting it up! . Curious to find out more or do you want to implement this in your own company? Then make sure to contact us. As a WatchGuard certified partner, we can help! This way you can take a huge leap forward in securing your environment and data in no time.
You can learn more about it on our page dedicated to this topic.
Our team of account managers is ready to help you

Christian

Jordan

Jurgen

Didier

Jean-Marc

Kaj





